Dual ISP - Cisco ASA HA Active/Standby
So a single ISP isn't cutting it anymore you need a backup just in case the primary fails and might as well add a second ASA into this design, more redundancy equals more up-time, right? On paper it sounds good but in the "real" world there probably is tipping point, more redundancy increases complexity. In this post we'll aim to keep it simple, with setting up a Cisco ASA HA active/standby pair and then add in the second ISP. Let's get started! So this is what our topology will look like all said and done, we have two firewalls and two different ISPs. The primary ISP is ISP-1 and the secondary ISP is ISP-2. We will always be using ISP-1 as the primary and won't be load balancing between the two. ISP-2 will only be used when ISP-1 goes offline. When ISP-1 comes back online we will switch back over to ISP-1.
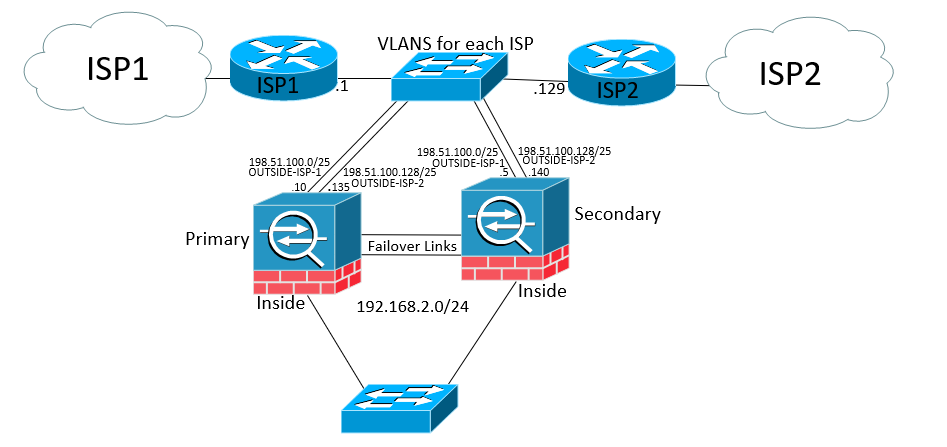
So let's first look at getting the ASA HA pair setup. In this example I have two ASA's that are the same hardware and software version, For the HA I have to be able to use two interfaces for the LAN failover and State link interface. I need to choose one ASA that will be the primary and one that is secondary. If you already have a configuration on one ASA, choose that as the primary. The secondary ASA just needs enough configuration so that you can get into it as the configuration gets overwritten on the secondary ASA from the primary.
ASA-HA-1(config)# failover
ASA-HA-1(config)# failover lan unit primary
ASA-HA-1(config)# failover
ASA-HA-1(config)# failover lan unit secondary
ASA-HA-1(config)# failover lan interface FAILOVER GigabitEthernet0/3
ASA-HA-1(config)# failover key password
ASA-HA-1(config)# failover link STATELINK GigabitEthernet0/4
ASA-HA-1(config)# failover interface ip FAILOVER 169.254.255.1 255.255.255.252 standby 169.254.255.2
interface GigabitEthernet0/0
nameif OUTSIDE-ISP-1
security-level 0
ip address 198.51.100.10 255.255.255.128 standby 198.51.100.5
!
interface GigabitEthernet0/1
nameif OUTSIDE-ISP-2
security-level 0
ip address 198.51.100.135 255.255.255.128 standby 198.51.100.140
!
ASA-HA-1(config)# route OUTSIDE-ISP-1 0.0.0.0 0.0.0.0 198.51.100.1 1 track 1
ASA-HA-1(config)# route OUTSIDE-ISP-2 0.0.0.0 0.0.0.0 198.51.100.129 254
Notice that I'm putting a distance metric on this route, this has a higher metric than the first default route so it won't be used until the primary route fails.
The track command will remove the primary route if it fails and then the ASA will install this the route in the routing table to switch over to the secondary ISP. We still have to configure some additional settings in order for this to work. We need to create an SLA on the ASA, in this example I'm using Google's Public DNS as a reachability test. If this was production setup I would probably use a system that I own instead of relaying one somebody else.
ASA-HA-1(config)# sla monitor 10
ASA-HA-1(config)# type echo protocol ipIcmpEcho 8.8.8.8 interface OUTSIDE-ISP-1
ASA-HA-1(config)# num-packets 5
ASA-HA-1(config)# frequency 10
ASA-HA-1(config)# sla monitor schedule 10 life forever start-time now
ASA-HA-1(config)# track 1 rtr 10 reachability
show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 198.51.100.1 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 198.51.100.1, OUTSIDE-ISP-1
C 169.254.255.0 255.255.255.252 is directly connected, FAILOVER
L 169.254.255.1 255.255.255.255 is directly connected, FAILOVER
C 192.168.2.0 255.255.255.0 is directly connected, INSIDE
L 192.168.2.50 255.255.255.255 is directly connected, INSIDE
C 198.51.100.0 255.255.255.128 is directly connected, OUTSIDE-ISP-1
L 198.51.100.10 255.255.255.255 is directly connected, OUTSIDE-ISP-1
C 198.51.100.128 255.255.255.128 is directly connected, OUTSIDE-ISP-2
L 198.51.100.135 255.255.255.255 is directly connected, OUTSIDE-ISP-2
ASA-HA-1# show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 198.51.100.129 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [254/0] via 198.51.100.129, OUTSIDE-ISP-2
C 169.254.255.0 255.255.255.252 is directly connected, FAILOVER
L 169.254.255.1 255.255.255.255 is directly connected, FAILOVER
C 192.168.2.0 255.255.255.0 is directly connected, INSIDE
L 192.168.2.50 255.255.255.255 is directly connected, INSIDE
C 198.51.100.0 255.255.255.128 is directly connected, OUTSIDE-ISP-1
L 198.51.100.10 255.255.255.255 is directly connected, OUTSIDE-ISP-1
C 198.51.100.128 255.255.255.128 is directly connected, OUTSIDE-ISP-2
L 198.51.100.135 255.255.255.255 is directly connected, OUTSIDE-ISP-2