FMC Syslog with Graylog Extractor
Let's continue to talk about the Cisco Firepower Management Center, in this post we are going to look at sending connection events over to syslog. In this example I'm using Graylog which is an open source logging platform and although any syslog server would work, one of the problems with syslogs is there is little uniformity when you have different systems sending these logs. One of the things that Graylog can to do is extract the raw message and put each part of message into a separate searchable field. We'll configure the FMC to send syslogs and then configure an extractor on Graylog.
So we have the FMC and Graylog in our environment setup. We'll want to first configure the FMC and add a syslog server. We can do this two ways, one way is we can go to into Policy tab-> Actions->Alerts->Create Alert (Down Arrow)->Create Syslog Alert.
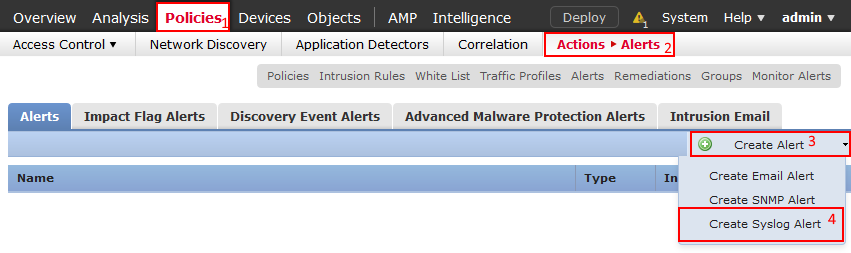
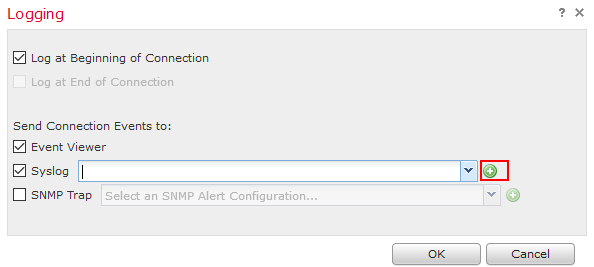
You could also go into an access control policy and select log ( ) icon either in the default action or on a rule you would like to log. Another window will show and select the green plus icon and add the syslog server that way.
) icon either in the default action or on a rule you would like to log. Another window will show and select the green plus icon and add the syslog server that way.
Once that is out-of-the-way we can now go into Graylog and configure an extractor on the syslog input. This is located under System->Inputs then under the syslog input select manage extractor. On the actions tab select import extractor and paste this JSON followed by selecting the Add extractors to input at the bottom of the page.
{
"extractors": [
{
"title": "FMC – Default Fields",
"extractor_type": "grok",
"converters": [],
"order": 15,
"cursor_strategy": "copy",
"source_field": "message",
"target_field": "",
"extractor_config": {
"grok_pattern": "%{WORD:field}: Protocol: %{WORD:protocol}, SrcIP: %{IP:Source_IP}, OriginalClientIP: ::, DstIP: %{IP:Destination_IP}, SrcPort: %{INT:src_port}, DstPort: %{INT:dest_port}, TCPFlags: %{WORD:flags}, IngressZone: %{HOSTNAME:ingress_zone}, EgressZone: %{HOSTNAME:egress_zone}, DE: %{DATA:detect_engine}, Policy: %{DATA:policy}, ConnectType: %{WORD:connectType}, AccessControlRuleName: %{DATA:ACLRuleName}, AccessControlRuleAction: %{DATA:ACLRuleAction},",
"named_captures_only": true
},
"condition_type": "regex",
"condition_value": "( SFIMS:)"
}
],
"version": "2.4.6"
}
_DMZ-FW02 SFIMS: Protocol: TCP, SrcIP: 172.25.45.55, OriginalClientIP: ::, DstIP: 172.25.30.82, SrcPort: 58996, DstPort: 1433, TCPFlags: 0x0, IngressZone: LOC-DMZ, EgressZone: LOC-INSIDE, DE: Primary Detection Engine (d4d9f400-c6d2-4065-9f90-da61a963b980), Policy: Acme DMZ ACP, ConnectType: Start, AccessControlRuleName: WEBSRVS->SQLSRVS->TCP1443, AccessControlRuleAction: Allow, Prefilter Policy: Default Prefilter Policy, UserName: No Authentication Required, InitiatorPackets: 2, ResponderPackets: 1, InitiatorBytes: 120, ResponderBytes: 66, NAPPolicy: Acme DMZ NAP, DNSResponseType: No Error, Sinkhole: Unknown, URLCategory: Unknown, URLReputation: Risk unknown_
ACLRuleAction
Allow
ACLRuleName
WEBSRVS->SQLSRVS->TCP1443
Destination_IP
172.25.30.82
Source_IP
172.25.45.55
connectType
Start
dest_port
1433
detect_engine
Primary Detection Engine (d4d9f400-c6d2-4065-9f90-da61a963b980)
egress_zone
LOC-INSIDE
field
SFIMS
flags
0x0
ingress_zone
LOC-DMZ
policy
Acme DMZ ACP
protocol
TCP
src_port
58996
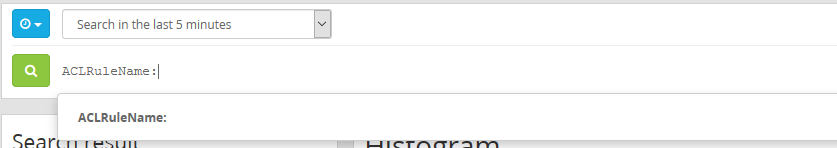
This makes it much easier to search these results as well as put this type of data into dashboards or reports. Like always I hope this information is helpful you can find more information about Graylog by hitting their site and try it out for yourself. :)