ASA Site to Site VPN (PATed)
If you ever needed to hide multiple systems behind a single IP address you would use PAT. (Port Address Translation) besides using this to connect to the internet when using an RFC 1918 address, you can configure PAT for VPN connections. The benefit is the same, hide multiple systems behind a single IP address with the advantage being you can have many systems on one side of the VPN tunnel all using that single IP.
In this example, we have a site to site VPN connection one side using a PATed public IP address. We originally have two systems that will be sending data over to Contoso who is the remote peer in this example. We are planning on adding additional systems in the future which is why Acme Corp is using a PATed address outbound. Contoso is expected to send data back to Acme Corp which will also be reflected in this example. Also note that the "public" IP addresses listed in this example are from RFC 5737 and are not publicly available. We have a need to setup a VPN to a partner and have agreed using a public IP address over the VPN connection. We are going to have multiple systems on the local side sending information over to this partner and because of that we're going to be using a single public PATed address instead of assigning multiple static NATed IPs to each system. The table below goes over the agreed settings and what networks are protected.
| Acme Corp | Contoso Ltd. |
|---|---|
| Peer IP Address: 192.0.2.10 | Peer IP Address: 203.0.113.10 |
| Phase 1: AES 256 SHA (Group 2) | Phase 1: AES 256 SHA (Group 2) |
| Phase 2: AES 128 SHA | Phase 2: AES 128 SHA |
| PFS: No | PFS: No |
| Protected Networks: 192.0.2.100/32 - PATed IP Address. 192.0.2.50/32 - IP Address Contoso will use when sending data to Acme. | Protected Networks: 203.0.113.30/32 - IP Address Acme will use when sending data to Contoso 203.0.113.50/32 - Contoso's source address when sending data back to Acme. |
| Preshared Key: cisco | Preshared Key: cisco |
Here is the topology for reference: 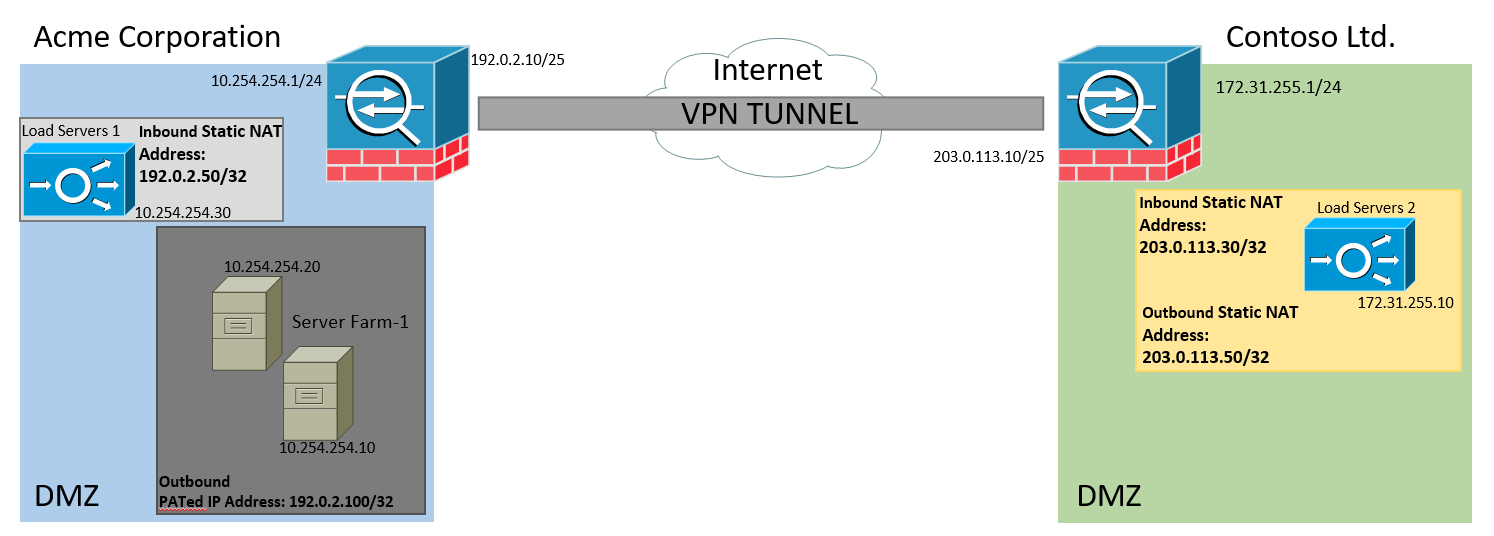
Let's start building the tunnel for Acme by creating some object groups:
object network ACCORP-DMZ-SERVER-1
host 10.254.254.10
object network Public-IP-192.0.2.100
host 192.0.2.100
object network VPN-CONTOSO-CLIENT-1
host 203.0.113.30
object network ACCORP-DMZ-SERVER-2
host 10.254.254.20
object network ACCORP-DMZ-LB-1
host 10.254.254.30
object network Public-IP-192.0.2.50
host 192.0.2.50
object network VPN-CONTOSO-CLIENT-2
host 203.0.113.50
object-group network ACCORP-DMZ-SERVERS
network-object object ACCORP-DMZ-SERVER-2
network-object object ACCORP-DMZ-SERVER-1
object-group network VPN-REMOTE-ACCORP-CONTOSO
network-object object VPN-CONTOSO-CLIENT-1
network-object object VPN-CONTOSO-CLIENT-2
object-group network VPN-LOCAL-ACCORP-CONTOSO
network-object object Public-IP-192.0.2.100
network-object object Public-IP-192.0.2.50
access-list ACL-VPN-ACCORP-CONTOSO extended permit ip object-group VPN-LOCAL-ACCORP-CONTOSO
nat (DMZ,Outside) source dynamic ACCORP-DMZ-SERVERS Public-IP-192.0.2.100 destination static VPN-CONTOSO-CLIENT-1 VPN-CONTOSO-CLIENT-1
nat (Outside,DMZ) source static VPN-CONTOSO-CLIENT-2 VPN-CONTOSO-CLIENT-2 destination static Public-IP-192.0.2.50 ACCORP-DMZ-LB-1 no-proxy-arp
group-policy GP-VPN-ACCORP-CONTOSO internal group-policy GP-VPN-ACCORP-CONTOSO attributes vpn-tunnel-protocol ikev1
tunnel-group 203.0.113.10 type ipsec-l2l tunnel-group 203.0.113.10 general-attributes default-group-policy GP-VPN-ACCORP-CONTOSO
tunnel-group 203.0.113.10 ipsec-attributes ikev1 pre-shared-key cisco isakmp keepalive disable
crypto map CM-ACCORP-CONTOSO 1 match address ACL-VPN-ACCORP-CONTOSO
crypto map CM-ACCORP-CONTOSO 1 set peer 203.0.113.10
crypto map CM-ACCORP-CONTOSO 1 set ikev1 transform-set ESP-AES-128-SHA
crypto map CM-ACCORP-CONTOSO 1 set nat-t-disable
crypto map CM-ACCORP-CONTOSO interface Outside
object network CONTOSO-DMZ-SERVER-1
host 172.31.255.10
object network PUBLIC-203.0.113.30
host 203.0.113.30
object network VPN-ACME-CLIENT-1
host 192.0.2.100
object network VPN-ACME-CLIENT-2
host 192.0.2.50
object network PUBLIC-203.0.113.50
host 203.0.113.50
object-group network VPN-LOCAL-CONTOSO-ACME
network-object object PUBLIC-203.0.113.30
network-object object PUBLIC-203.0.113.50
object-group network VPN-REMOTE-CONTOSO-ACME
network-object object VPN-ACME-CLIENT-1
network-object object VPN-ACME-CLIENT-2
access-list ACL-VPN-CONTOSO-ACME extended permit ip object-group VPN-LOCAL-CONTOSO-ACME object-group VPN-REMOTE-CONTOSO-ACME
nat (Outside,DMZ) source static VPN-ACME-CLIENT-1 VPN-ACME-CLIENT-1 destination static PUBLIC-203.0.113.30 CONTOSO-DMZ-SERVER-1 no-proxy-arp
nat (DMZ,Outside) source static CONTOSO-DMZ-SERVER-1 PUBLIC-203.0.113.50 destination static VPN-ACME-CLIENT-2 VPN-ACME-CLIENT-2 no-proxy-arp
group-policy GP-VPN-ACME-CONTOSO internal group-policy GP-VPN-ACME-CONTOSO attributes vpn-tunnel-protocol ikev1
tunnel-group 192.0.2.10 type ipsec-l2l tunnel-group 192.0.2.10 general-attributes default-group-policy GP-VPN-ACME-CONTOSO
tunnel-group 192.0.2.10 ipsec-attributes ikev1 pre-shared-key cisco isakmp keepalive disable\
crypto map CM-CONTOSO-ACME 1 match address ACL-VPN-CONTOSO-ACME
crypto map CM-CONTOSO-ACME 1 set peer 192.0.2.10
crypto map CM-CONTOSO-ACME 1 set ikev1 transform-set ESP-AES-128-SHA
crypto map CM-CONTOSO-ACME 1 set nat-t-disable
crypto map CM-CONTOSO-ACME interface Outside
cisco@ACCORP-DMZ-Server-2:~$ ping 203.0.113.30
PING 203.0.113.30 (203.0.113.30) 56(84) bytes of data.
64 bytes from 203.0.113.30: icmp_seq=2 ttl=64 time=3.08 ms
64 bytes from 203.0.113.30: icmp_seq=3 ttl=64 time=1.52 ms
64 bytes from 203.0.113.30: icmp_seq=4 ttl=64 time=2.39 ms
64 bytes from 203.0.113.30: icmp_seq=5 ttl=64 time=1.94 ms
64 bytes from 203.0.113.30: icmp_seq=6 ttl=64 time=2.08 ms
64 bytes from 203.0.113.30: icmp_seq=7 ttl=64 time=3.38 ms
64 bytes from 203.0.113.30: icmp_seq=8 ttl=64 time=2.78 ms
64 bytes from 203.0.113.30: icmp_seq=9 ttl=64 time=3.16 ms
64 bytes from 203.0.113.30: icmp_seq=10 ttl=64 time=1.81 ms
^C
--- 203.0.113.30 ping statistics ---
10 packets transmitted, 9 received, 10% packet loss, time 9018ms
rtt min/avg/max/mdev = 1.525/2.465/3.389/0.627 ms
cisco@ACCORP-DMZ-Server-2:~$
cisco@CONTOSO-DMZ-Server-1:~$ ping 192.0.2.50
PING 192.0.2.50 (192.0.2.50) 56(84) bytes of data.
64 bytes from 192.0.2.50: icmp_seq=2 ttl=64 time=1.82 ms
64 bytes from 192.0.2.50: icmp_seq=3 ttl=64 time=1.82 ms
64 bytes from 192.0.2.50: icmp_seq=4 ttl=64 time=1.84 ms
64 bytes from 192.0.2.50: icmp_seq=5 ttl=64 time=1.69 ms
64 bytes from 192.0.2.50: icmp_seq=6 ttl=64 time=1.72 ms
64 bytes from 192.0.2.50: icmp_seq=7 ttl=64 time=1.74 ms
64 bytes from 192.0.2.50: icmp_seq=8 ttl=64 time=2.16 ms
64 bytes from 192.0.2.50: icmp_seq=9 ttl=64 time=3.86 ms
64 bytes from 192.0.2.50: icmp_seq=10 ttl=64 time=1.70 ms
64 bytes from 192.0.2.50: icmp_seq=11 ttl=64 time=2.82 ms
^C
--- 192.0.2.50 ping statistics ---
11 packets transmitted, 10 received, 9% packet loss, time 10025ms
rtt min/avg/max/mdev = 1.697/2.121/3.863/0.667 ms
cisco@R-DMZ-Server-2:~$
ASA-1# show crypto isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 203.0.113.10
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
ASA-2# show crypto isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 192.0.2.10
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
That's all I got, I hope this information is helpful. If you are using Cisco VIRL/CML here is a link on GitHub