Configuring AAA – Locally
 A while back I talked about AAA but never put out a post on how configure it until now. In this post I am going to be going over the configuration steps of how to configure AAA locally on a Cisco router, (The same commands would also work on Cisco switch). To review what exactly AAA does check my earlier post Understanding AAA. Like mentioned in my earlier post of Understanding AAA it gets better if you have some type of radius or tacacs+ server. Let's at least take look at configuring it locally first and I'll be sure to include another post on configuring a radius and tacacs+ server.
A while back I talked about AAA but never put out a post on how configure it until now. In this post I am going to be going over the configuration steps of how to configure AAA locally on a Cisco router, (The same commands would also work on Cisco switch). To review what exactly AAA does check my earlier post Understanding AAA. Like mentioned in my earlier post of Understanding AAA it gets better if you have some type of radius or tacacs+ server. Let's at least take look at configuring it locally first and I'll be sure to include another post on configuring a radius and tacacs+ server.
So I have a router called BRANCH-1 and below is the running-config. In this configuration you will notice a couple of things I first don't have aaa enabled. In this configuration I do a local username on the device called admin with a secret password, and on the VTY lines I have enabled the router to check the local database when connecting on those lines along with an enable secret password.
BRANCH-1#show run
Building configuration...
Current configuration : 1456 bytes
!
version 12.3
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname BRANCH-1
!
boot-start-marker
boot-end-marker
## ENABLE SECRET PASSWORD (LINE 16)##
enable secret 5 (MD5 Hashed Password)
!
## LOCAL USERNAME AND PASSWORD (LINE 19)##
username admin privilege 15 secret 5 (MD5 Hashed Password)
clock timezone PCTime -7
clock summer-time PCTime date Apr 6 2003 2:00 Oct 26 2003 2:00
no network-clock-participate aim 0
no network-clock-participate aim 1
## AAA NOT ENABLED (LINE 25)##
no aaa new-model
!ip subnet-zero
!
!
ip cef
ip dhcp excluded-address 192.168.40.0 192.168.40.5
!
ip dhcp pool DHCP-40-POOL
network 192.168.40.0 255.255.255.0
dns-server 208.67.222.222
default-router 192.168.40.1
domain-name BRANCH1.CISCOSKILLS.NET
!
!
ip ips po max-events 100
no ftp-server write-enable
!
!
!
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.40.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/0/0
ip address 192.168.20.6 255.255.255.252
no fair-queue
!
interface Serial0/0/1
ip address 192.168.20.10 255.255.255.252
!
router rip
version 2
passive-interface FastEthernet0/0
passive-interface FastEthernet0/1
network 192.168.20.0
network 192.168.40.0
no auto-summary
!
ip classless
ip http server
ip http authentication local
ip http secure-server
!
!
!
!
control-plane
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
## CHECK THE LOCAL USERNAME AND PASSWORD BEFORE ACCESS (LINE 91)##
login local
transport input telnet ssh
!
scheduler allocate 20000 1000
!
end
BRANCH-1#config t
Enter configuration commands, one per line. End with CNTL/Z.
BRANCH-1(config)#aaa new-model
If we type aaa authentication and put a question mark at the end you can see the available commands we can use. You can definitely customize a lot of features. :) ``` BRANCH-1(config)#aaa authentication ? arap Set authentication lists for arap. attempts Set the maximum number of authentication attempts banner Message to use when starting login/authentication. dot1x Set authentication lists for IEEE 802.1x. enable Set authentication list for enable. eou Set authentication lists for EAPoUDP fail-message Message to use for failed login/authentication. login Set authentication lists for logins. password-prompt Text to use when prompting for a password ppp Set authentication lists for ppp. sgbp Set authentication lists for sgbp. username-prompt Text to use when prompting for a username
Let's focus on setting up the ability of logging into the device so if we type **aaa authentication login** we can see two options on BRANCH-1. The "WORD" option is what we will use when setting up a custom method list, for this example we will use the default method list. Which looks at the console, auxiliary lines and VTY lines.
So let's go through this command again with the following, **aaa authentication login default** and follow that by a question mark. We have a couple of options to work with on BRANCH-1. This basically wants to know what password do you want use? You could use the enable password, or use a server-group for radius or tacacs+ authentication and more. You could also use these methods for redundancy check let's say you use a server-group but it is unreachable if you don't have another method for login we won't be able to connect to this device.
For this example we are just going to use the local database that is stored on the router the running-config. So are command would be **aaa authentication login default local**. Which tells the router to use the default method list and the password we want to use is located on the router.
So what does this do? If we exit out of the router we will be prompted with login prompt at the console. We will also be prompted if we connected with telnet or SSH connection and be required to type a username and password before we get access to the device.
Press RETURN to get started.
User Access Verification
Username: admin Password:
We can make our own method list, say for example we wanted the ability to not be prompted with a user name or password when we are connected to a console connection but be prompted when we attempt to connect with either telnet or SSH connection we can do that ;). We first have to create two authentication lists. The first one will be called OPEN-CON with none at the end which tells the router don't check anything for verification and just open it up. The second authentication list will be called LOCAL-DB with local at the end which checks the running-config for a username and password and it must match before it allows it any further.
We now have to apply these method lists to the correct lines on the router. The OPEN-CON is going on the console line under "line con 0" below is the command to apply it.
When I attempt to login the router from the console I don't have to type a password to get into it, except for the enable secret password.
Now let's apply the last method list we have created called LOCAL-DB which will check the local database for a valid username and password before granting access we will apply this to the VTY lines 0 through 4 below is the command to apply it.
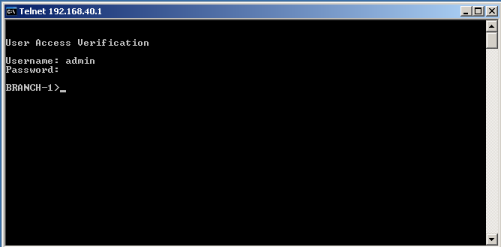 To review we have we went over creating AAA locally on our router or switch, we talked about using the just the default method list and we also covered created our own method lists to which we applied to the console and VTY lines.
To review we have we went over creating AAA locally on our router or switch, we talked about using the just the default method list and we also covered created our own method lists to which we applied to the console and VTY lines.
Since each were using a different method list, different login results happened. On the console we were presented with no username and password and just the enable secret password. When we attempted to login into the one of the VTY lines by using telnet and or SSH we were required to type a username and password before gaining entry to the router or switch. Like always I hope this information is helpful and comment below if you have questions and or feedback.
Related articles
- Introduction into Cisco Configuration Professional (ryansrealm.com/ciscoskills)
- Using a Cisco 2600 Router at Home (joedissmeyer.com)